What is a “Legacy” Application?
Microsoft defines any application which can run on older versions of Windows® as a “legacy” application — because Microsoft would prefer that all computers pay a license fee for the “latest and greatest” (free of concern for hardware & software upgrade costs). Microsoft makes money from Windows® and Office® upgrades, but businesses and users lose that amount plus hardware replacement costs. Syscob believes that the system used by a client should be decided by their business policies and not be dictated by a software vendor. So all Syscob export applications are designed to run on any OS version from Windows NT4 or Windows 95 through Windows Server 2008 R2 or Windows 7. Meaning that Export-It and Export-It Plus are, by Microsoft's definition, “legacy” applications.
Windows 7 Security versus “Legacy” Applications
To illustrate how the numerous security changes for users, file & Registry access and networks can impact “legacy” applications the best point to start is with a fresh, defaults installation of Windows 7 on a new PC. After installing Windows 7 Professional (Microsoft recommendation for workstations on a business network), with only the single user named “Syscob User” entered during setup, the Desktop looks like this:
It is also important to note that this is “32-bit” Windows® software, as can be seen in the System applet of the Control Panel (capture below). Syscob applications for exporters are “32-bit” software. That means that if they are to be used on a “64-bit” version of Windows 7 then the new “XP Mode” feature for Windows 7 must be downloaded and installed on the PC and then the Syscob software installed in the XP Mode virtual machine. Neither Export-It nor Export-It Plus will run in a native “64-bit” Windows® environment.

The user entered during setup is a member of the Administrators security group, as for past versions of Windows® software. This can be confirmed by checking the properties of the Administrators security group, as below, or the “Member Of” tab for the Syscob User properties.

However, despite the assurance that “Administrators have complete and unrestricted access to the computer/domain” (above), this is no longer true for Windows 7! For example, the Administrators security group no longer “owns” the Windows® directory and has severely restricted privileges under Windows 7 default security settings.
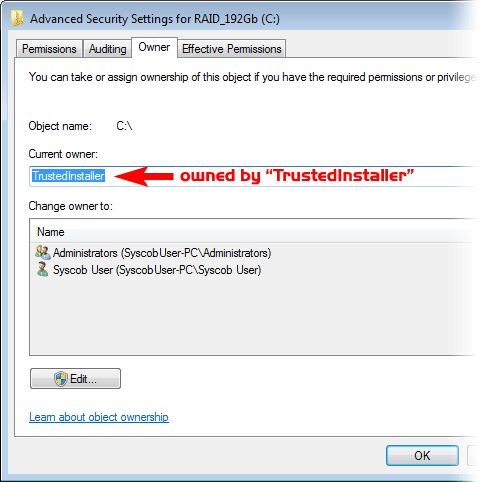
The first capture below shows that the “system” [boot] drive () is now owned by TrustedInstaller (a service), not by the Administrators group as in prior versions. That could be a problem except for the fact that the Administrators security group is granted “Full Control” file access permissions to the drive's root directory (as seen in the second capture below).
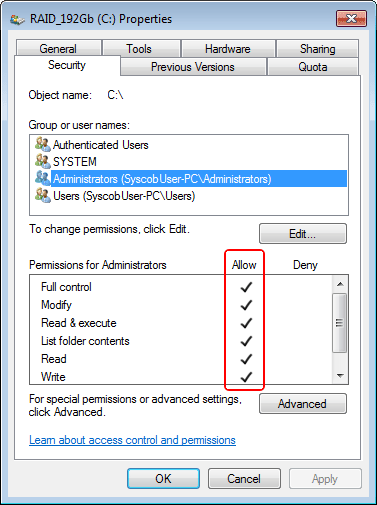
In the capture above the file access permissions for the [root] directory of the boot drive are highlighted. The fact that the Administrators security group, of which Syscob User is a member, has “Full Control” access means that the user can create or delete or modify files and folders on the disk — unless a particular file or folder has explicit file access restrictions defined! (e.g. the Windows® directory).
Windows® Folder Restrictions on Administrators
As the first capture below demonstrates, TrustedInstaller also “owns” the Windows® directory. But, unlike the “system drive” root folder, it grants only extremely limited “special” permissions to even the Administrators group!


The extreme restrictions (visible in the capture above) not only prevent an administrative user from accessing the Windows® directory and its files and subfolders, but they also have catastrophic impacts on “legacy” applications like Export-It and Export-It Plus!
In prior versions of Windows® Microsoft advised that applications should keep their settings in an “INI” file in the Windows® folder, but that is no longer possible with default Windows 7 security settings. Nor is free access to the “Printers and Faxes” defined for a Windows® system.
The impact of these security changes will be exposed by running the Syscob eExamine wizard that is downloadable from the Syscob web site. See the “Identifying security issues before deploying “legacy” applications” topic for a demonstration of how the Syscob eExamine wizard finds these issues and recommends actions needed to correct them before a “legacy” application is deployed.